A Deep Dive into Cybersecurity: Man-in-the-Middle(MiMT) Attacks
Introduction
In today’s interconnected digital world, the importance of cybersecurity cannot be overstated. As more of our personal and professional lives move online, the risks associated with cyber threats continue to grow. One particularly insidious type of attack is the Man-in-the-Middle (MitM) attack, a sophisticated form of cyber intrusion where an attacker secretly intercepts and potentially alters the communication between two parties. This kind of attack can have devastating consequences, leading to data breaches, financial loss, and compromised personal information.
Man-in-the-Middle attacks have been a persistent threat since the early days of networking, and they continue to evolve as technology advances. Understanding how these attacks work, the different types of MitM attacks, and how to protect against them is crucial for anyone concerned about cybersecurity. In this blog post, we’ll delve into the mechanics of Man-in-the-Middle attacks, explore various methods used by attackers, and discuss strategies to safeguard against these threats.
What is a Man-in-the-Middle Attack?
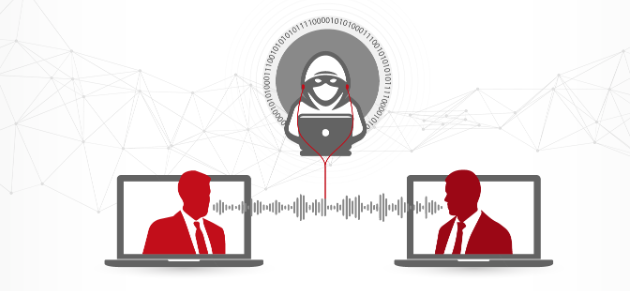
A Man-in-the-Middle attack occurs when a malicious actor inserts themselves into a communication between two parties, typically without their knowledge. The attacker can then eavesdrop on the communication, intercept and potentially alter the messages being sent, or steal sensitive information such as login credentials or credit card details.
The name “Man-in-the-Middle” comes from the attacker’s position—literally in the middle—between the two parties. Unlike other forms of attacks where the target is directly compromised (e.g., malware on a device), MitM attacks are subtler and often harder to detect because they exploit the trust between the two communicating parties.
Types of Man-in-the-Middle Attacks
Man-in-the-Middle attacks can take several forms, each with its own method of execution. Here are some of the most common types:
1. Eavesdropping
In this type of attack, the attacker simply listens in on the communication between two parties. This can be done on unencrypted networks, where data is transmitted in plain text. For example, if you’re using public Wi-Fi that isn’t secured, an attacker could potentially intercept your data, including sensitive information like passwords or bank account details.
2. Session Hijacking
Session hijacking involves taking control of a user’s session after they have authenticated themselves on a website. This typically occurs when an attacker steals a session cookie, which is used by a web server to recognize that a user is logged in. Once the attacker has the session cookie, they can impersonate the user and access their account.
3. SSL Stripping
SSL (Secure Sockets Layer) is a protocol used to encrypt data transmitted between a web browser and a server. SSL stripping is a technique where an attacker downgrades the communication from HTTPS (secure) to HTTP (insecure). This allows the attacker to intercept and read the data in plain text, which would otherwise be encrypted.
4. DNS Spoofing
DNS (Domain Name System) is like the phonebook of the internet, translating human-friendly domain names into IP addresses. In a DNS spoofing attack, the attacker corrupts the DNS server’s response so that the user is directed to a fraudulent website instead of the intended one. This fake site may look identical to the real one, but its purpose is to steal sensitive information, such as login credentials.
5. Wi-Fi Eavesdropping
Public Wi-Fi networks, particularly those that are not secured, are prime targets for MitM attacks. Attackers can set up rogue Wi-Fi hotspots with names similar to legitimate ones (known as “evil twins”). Unsuspecting users may connect to these rogue networks, giving attackers full visibility into their online activities.
Check Also
How Do Man-in-the-Middle Attacks Work?
The execution of a Man-in-the-Middle attack typically involves a few key steps:
- Interception: The attacker first intercepts the communication between the two parties. This can be done through various means, such as exploiting a vulnerability in a Wi-Fi network, DNS spoofing, or using malware to gain access to a device.
- Decryption (if necessary): If the communication is encrypted, the attacker must decrypt it to gain access to the information. SSL stripping is a common technique used for this purpose.
- Modification: Once the attacker has access to the communication, they can choose to simply eavesdrop, or they might modify the data before sending it on to the intended recipient. For example, an attacker could alter a bank transaction by changing the account number to which funds are being transferred.
- Relay: After potentially altering the communication, the attacker sends it on to the original destination, often leaving the two parties unaware that their communication has been compromised.
Real-World Examples of Man-in-the-Middle Attacks
MitM attacks have been used in various real-world scenarios, from sophisticated government surveillance operations to simple attacks on public Wi-Fi users.
- Stuxnet Worm: This infamous cyber-weapon used a MitM attack to infect Iranian nuclear facilities, altering the data sent to operators so they believed everything was functioning normally while the worm was causing physical damage to equipment.
- Superfish Scandal: In 2015, it was discovered that certain Lenovo laptops were shipped with a program called Superfish, which installed a self-signed root certificate, allowing it to intercept and decrypt HTTPS traffic—a classic MitM scenario.
How to Protect Against Man-in-the-Middle Attacks
Defending against MitM attacks requires a multi-layered approach:
- Encryption: Always use secure, encrypted connections (HTTPS) when transmitting sensitive information. Avoid using public Wi-Fi networks for transactions or logging into sensitive accounts.
- Public Wi-Fi Caution: Be cautious when connecting to public Wi-Fi networks. Use a VPN (Virtual Private Network) to encrypt all data traffic, ensuring that even if it’s intercepted, it cannot be read.
- Secure DNS: Utilize DNS over HTTPS (DoH) or DNS over TLS (DoT) to ensure that DNS queries are encrypted and less vulnerable to spoofing.
- Strong Authentication: Implement strong, multi-factor authentication (MFA) methods to prevent attackers from easily hijacking sessions.
- Regular Software Updates: Ensure that all devices, browsers, and applications are regularly updated to protect against known vulnerabilities that could be exploited in a MitM attack.
- Use of Security Certificates: Check for valid security certificates when accessing websites. An SSL certificate helps confirm that the website you’re visiting is legitimate and not a spoof.
Conclusion
Man-in-the-Middle attacks represent a significant threat in the world of cybersecurity, exploiting trust and vulnerabilities in communication channels to intercept, alter, or steal sensitive information. As these attacks continue to evolve, it is crucial for individuals and organizations alike to stay informed about the risks and to implement robust security measures to protect their data. By understanding the mechanisms behind MitM attacks and adopting best practices for online security, we can significantly reduce the likelihood of falling victim to these stealthy and dangerous cyber threats.